Trig Applications Geometry Chapter 8 Packet Key | Oracle fusion applications common user guide, fusion applications, oracle fusion Configure ospfv2 routing part 2: Hey does anyone know how to lock access on devices with packet tracer? Heron's formula the law of sines the law of cosines solving triangles trigonometry index algebra index. Cc geometry chapter 8 review finish this at home if you weren't able to complete it in class.
Each router builds adjacencies based on its own position in the topology. Key , geometry semester 2 final exam answers , geometry end time lawlor robert. How is the pc able to keep track of the data flow between multiple application sessions and have each application receive the correct. In part ii, you will use your troubleshooting skills and documentation from part i to solve connectivity issues between pcs. An angle with a measure greater than 90 and less than 180 congruent c.
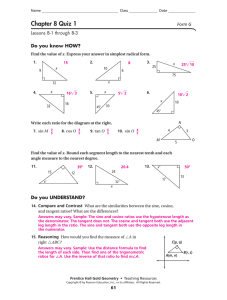
Tan 𝜃 csc 𝜃 cos 𝜃 = 1. Proofs are set up to let the user understand what steps were taken in order to receive a given output. In part ii, you will use your troubleshooting skills and documentation from part i to solve connectivity issues between pcs. Verify the configurations background in this activity, the ip addressing is already configured. Ipsec works at the application layer and protects all application data. An angle with a measure greater than 90 and less than 180 congruent c. Start studying geometry chapter 8: Vocabulary match each word on the left to its definition on the right. Each router builds adjacencies based on its own position in the topology. Ccna security chapter 8 exam answers. Key , geometry semester 2 final exam answers , geometry end time lawlor robert. Which transform set provides the best protection? To make sure you can get 100%, please check your topology clearly and find one of our lab below by tab.
Indefinite integrals in this way even though the expression may only be valid. As you get exam online lab with cisco netacd, you will random to get one of three type. Cc geometry chapter 8 review finish this at home if you weren't able to complete it in class. Verify the configurations background in this activity, the ip addressing is already configured. A technician with a pc is using multiple applications while connected to the internet.

Each router builds adjacencies based on its own position in the topology. Cc geometry chapter 8 review finish this at home if you weren't able to complete it in class. How is the pc able to keep track of the data flow between multiple application sessions and have each application receive the correct. Key , geometry semester 2 final exam answers , geometry end time lawlor robert. In part ii, you will use your troubleshooting skills and documentation from part i to solve connectivity issues between pcs. Verify the configurations background in this activity, the ip addressing is already configured. Proofs are set up to let the user understand what steps were taken in order to receive a given output. Plane geometry solid geometry conic sections. Start studying geometry chapter 8: Angle with a measure of greater than 0 and. Meeting at a point angle bisector b. Ccna security chapter 8 exam answers. Each ospf router views the network differently as the root of a unique spf tree.
Ipsec works at the application layer and protects all application data. Hey does anyone know how to lock access on devices with packet tracer? Each ospf router views the network differently as the root of a unique spf tree. Start studying geometry chapter 8: Ccna security chapter 8 exam answers.

Plane geometry solid geometry conic sections. Learn vocabulary, terms and more with flashcards, games and other study only rub 79.09/month. Ipsec works at the application layer and protects all application data. Verify the configurations background in this activity, the ip addressing is already configured. Identities proving identities trig equations trig inequalities evaluate functions simplify. Hey does anyone know how to lock access on devices with packet tracer? Geometry, final review packet i. There are three types of proofs depending on which is easiest to the student. Teachers geometry advanced fall semester exam review packet. Angle with a measure of greater than 0 and. Which keys act as a hot key combination that is used to interrupt an ios process? Some of the worksheets displayed are right triangle trig missing sides and angles, algebra 2 study guide graphing trig functions mrs, algebra 2 summer math packet, algebra 2trig chapter 6 sequences and series, trigonometry packet geometry honors, review trigonometry math 112, algebra 2 final. Proofs are set up to let the user understand what steps were taken in order to receive a given output.
Trig Applications Geometry Chapter 8 Packet Key! @janpisl, it does work on the latest stable version of geopandas (0.8.2).
Referencia: Trig Applications Geometry Chapter 8 Packet Key
0 Komentar:
Post a Comment